The vulnerability management landscape has become overwhelming. With over 25,000 CVEs published in 2022 alone, security teams are drowning in a sea of severity scores that often don’t reflect real-world risk. It’s time to move beyond traditional CVSS-based approaches and focus on what actually matters.
The Vulnerability Explosion Problem
The numbers are staggering; Since 2000, we’ve seen over 200,000 published CVEs, with the annual count growing from around 1,000 in the early 2000s to over 25,000 in recent years. This exponential growth has created a critical challenge for security teams.
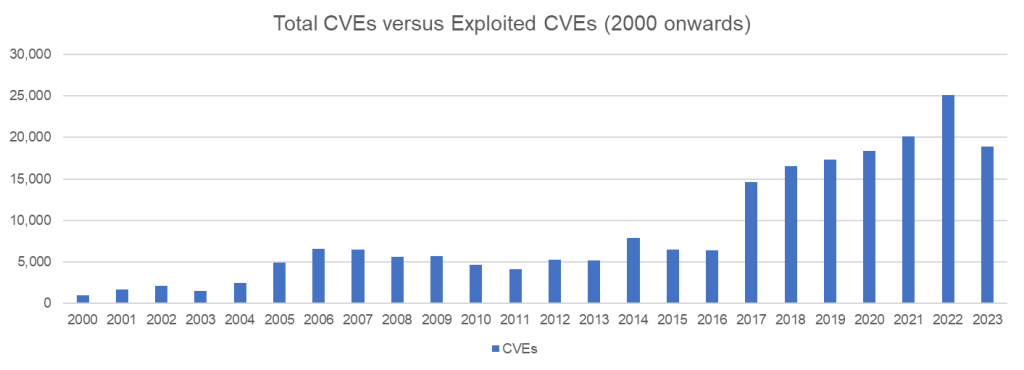
The real question isn’t “How many vulnerabilities exist?” but rather “Which ones actually pose a threat to my organisation?”
Why CVSS Scores Fall Short
CVSS Base Scores are designed to measure the technical severity of vulnerabilities, but they don’t account for:
- Whether the vulnerability is actually exploitable in your environment
- If there are active exploits in the wild
- The likelihood of future exploitation
- Your organisation’s specific risk profile
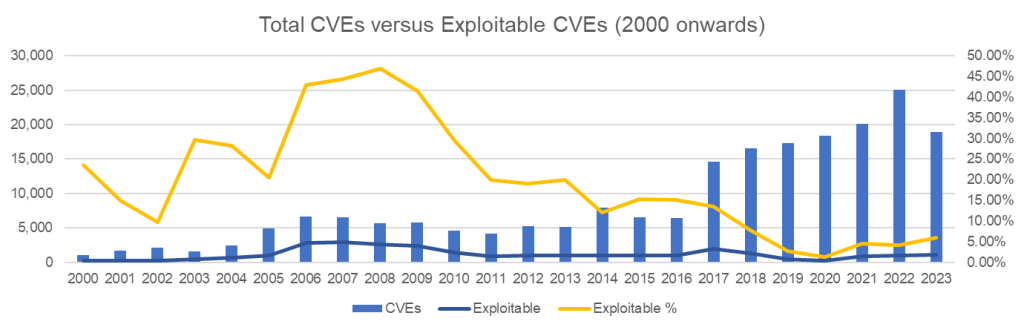
The result; Teams waste time patching high-severity vulnerabilities that pose little real risk while missing lower-severity vulnerabilities that are actively being exploited.
A Better Approach: KEV and EPSS
CISA’s Known Exploited Vulnerabilities (KEV) catalog identifies vulnerabilities that are actively being exploited in the wild. These represent clear and present danger to organisations.
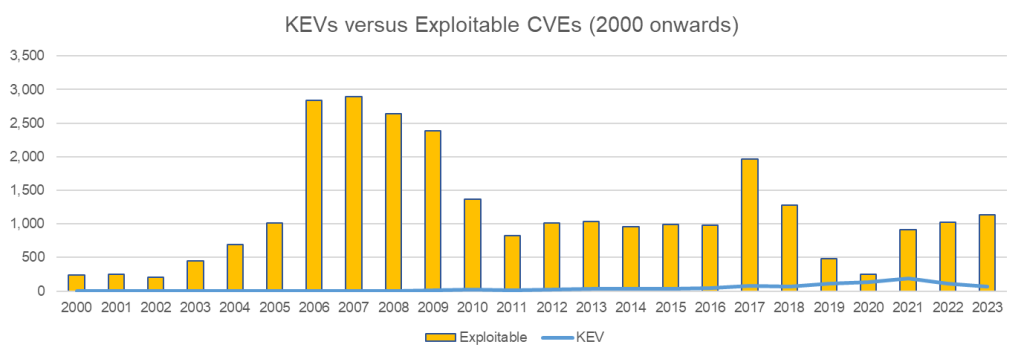
The Exploit Prediction Scoring System (EPSS) uses machine learning to predict which vulnerabilities are likely to be exploited in the next 30 days, giving you a head start on remediation.
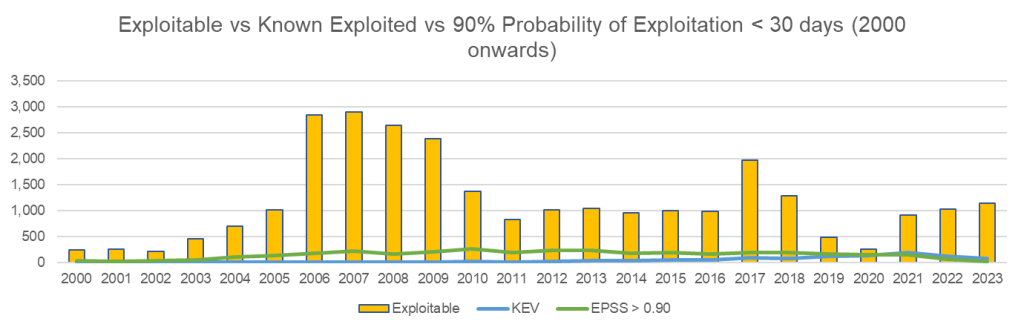
Combined, these tools help you focus on the vulnerabilities that actually matter:
| Year | Total CVEs | Exploitable | KEV | EPSS > 0.90 |
| 2020 | 18,350 | 251 (1.37%) | 131 | 143 |
| 2021 | 20,158 | 911 (4.52%) | 187 | 145 |
| 2022 | 25,101 | 1,023 (4.08%) | 117 | 64 |
| 2023 | 18,914 | 1,137 (6.01%) | 69 | 20 |
Note: Some CVEs appear in multiple categories, so these numbers aren’t mutually exclusive.
Implementing a Risk-Based Triage Process
Step 1: Immediate Action Items
- Prioritise all vulnerabilities on the KEV list
- Assess their relevance to your environment
- Schedule immediate remediation for applicable items
Step 2: High-Probability Threats
- Review vulnerabilities with EPSS scores above 0.90
- Evaluate their potential impact on your systems
- Plan remediation within 30 days
Step 3: Theoretical Exploits
- Assess remaining exploitable vulnerabilities
- Consider your specific threat landscape
- Schedule based on business risk and available resources
The CVE-2023-26083 Case Study
This vulnerability perfectly illustrates why traditional scoring fails:
- CVSS Score: 3.3 (Low severity)
- EPSS Score: 0.001 (less than 1% chance of exploitation)
- Reality: Actively exploited by spyware vendors targeting Android devices
The lesson: Even “low” severity vulnerabilities can pose significant risk when they’re actively being exploited. This is why KEV and EPSS are more valuable than CVSS scores alone.
Building a Holistic Vulnerability Management Strategy
Asset Categorisation is crucial for effective prioritisation:
- Identify your most critical systems
- Understand your attack surface
- Focus remediation efforts where they matter most
Clear Roles and Responsibilities ensure accountability:
- Define who owns each system or application
- Establish clear remediation timelines
- Create escalation procedures for high-risk vulnerabilities
Diversified Intelligence Sources provide comprehensive coverage:
- Don’t rely solely on one vulnerability database
- Monitor CVE Numbering Authorities (CNAs) directly
- Subscribe to threat intelligence feeds relevant to your industry
Effective Communication translates technical risks into business language:
- Present vulnerabilities in terms of business impact
- Align security initiatives with organisational objectives
- Get buy-in from leadership for necessary remediation efforts
Australian-Specific Considerations
Essential Eight compliance requires a risk-based approach to vulnerability management:
- Focus on vulnerabilities that could compromise Essential Eight controls
- Prioritise patches that improve your overall security posture
- Document your risk assessment process for audit purposes
Privacy Act requirements mean considering data exposure risks:
- Prioritise vulnerabilities that could lead to data breaches
- Consider the sensitivity of data stored on affected systems
- Ensure your triage process supports breach notification requirements
Common Pitfalls to Avoid
Don’t ignore low-severity vulnerabilities that are actively being exploited – severity and exploitability are different things.
Don’t rely on a single source for vulnerability intelligence – diversify your information sources.
Don’t forget about your specific environment – a vulnerability that’s critical for one organisation might be irrelevant for another.
Don’t skip the business context – technical severity doesn’t always translate to business risk.
The Bottom Line
Effective vulnerability management isn’t about patching everything – it’s about patching the right things at the right time. By focusing on KEV and EPSS rather than CVSS scores alone, you can:
- Reduce the noise in your vulnerability management process
- Focus resources on threats that actually matter
- Improve your overall security posture
- Make better risk-based decisions
The goal isn’t to eliminate every vulnerability, but to ensure that the vulnerabilities that pose real risk to your organisation are addressed promptly and effectively.
Ready to transform your vulnerability management process? Start by integrating KEV and EPSS into your existing workflow, then gradually build out the supporting processes that make risk-based prioritisation effective.
